Default
Stack Based Buffer Overflow
Memory Corruption
Modifying memory of a binary in a way that was not intended.
Buffer Overflow
A buffer overflow occurs when data is written beyond the allocated memory space, thus corrupting adjacent memory.
Common Causes:
- Unsafe functions: These functions do not perform any bounds checking when writing to a fixed-size buffer. These functions include:
- strcpy
- gets
- sprintf
Impact:
- Arbitrary Code Execution (if return address is overwritten)
- Denial of service.
- Data corruption
Example
1
2
3
4
5
6
7
8
9
10
11
int main() {
int x;
char buffer[32];
gets(buffer);
if (x = 0xdeadbeef) {
puts("You win.");
} else {
puts("You lose.");
}
return 0;
}
Stack before gets function
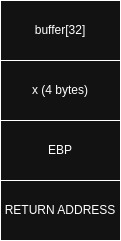
if we enter more than 32 bytes the x variable will be overwritten. So we have to enter 32 bytes that will fill the buffer and then another 4 0xdeadbeef to overwrite x
Stack after the gets function
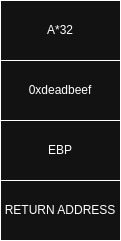
0xdeadbeef must be in least significant bit
exploit :